Memory forensics Challenge (Letsdefend)
Hi guys, i made this windows memory forensics challenge which was published on letsdefend. I am writing this writeup in the intended way to solve the challenge using volatility 3. We will learn to analyse windows processes and find hidden malware among the processes. We will go through full memory forensics process.
We see that we have a .mem file

We will use vollatility3 for analysing this memory dump , although i prefer volatility2 but it requires us to specify exact os build of the memory dump which is bit of hassle so we will just use volatiliy3.
Q1 What was the date and time when Memory from the compromised endpoint was acquired?
we see windows information through windows.info plugin

We can see the system time , and surely its the time when ram snapshot was taken
Answer : 2022–07–26 18:16:32
Q2 What was the suspicious process running on the system? (Format : name.extension)
Ok so lets analyse the active processes at time of acquistion .
Volatiltity has multiple options for listing processes like windows.pslist, windows.pstree, windows.psscan. I wont go in details of each but for our purpose pstree and pslist are enough.
Now we must know what processes are normal on a windows host. As the saying goes, “Know Normal to find evil”. If we know the normal processes we can filter out any suspicious processes to further analyse them. A great resource for this is SANS famous hunt evil cheatsheet
https://www.sans.org/posters/hunt-evil/
After we have all the processes , we can see mutiple svchosts processes which may seem abnormal to beginners but it is normal to have atleast 8–10 svchosts processes on windows boot. wininit,smss,csrss,services,lsass , these all processes are important for a windows system to run.
But attackers can trick us by renaming the malware executables as windows legit binaries name like , services.exe,svchosts.exe,lsass.exe etc. So its important to verify that a process has a parent process which is legit for example svchost.exe should always have parent process of services.exe, and lsass.exe should have wininit.exe. So if we use pstree plugin and have a heirarichal view we can see that there’s multiple svchosts but its normal. we also spot 2 lsass.exe which is absolutely suspicious. There should be only 1 lsass process and its parent process should be always wininit.exe . If we look at each process we spot 2 lsass process,

we see that first lsass.exe has process id of 640 and its parent process id is 500 . Now lets see what process has PID of 500
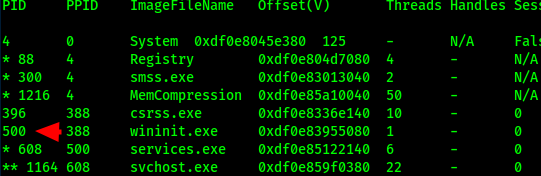
Its wininit.exe which is legit. Lets analyse the next lsass.exe
So the second lsass.exe has parent process id is 3996 and we can see since its a tree view its child process of explorer.exe . We can also verify it by PID and PPID. lsass shouldnt have explorer as its parent process . So we know something fishy is going on
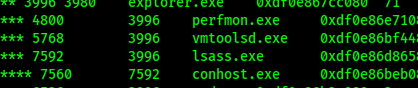
We can safely say that this is a malicious process
Answer : lsass.exe
Q3 Analyze and find the malicious tool running on the system by the attacker
Now we need to analyse this malicious process and need to find name of this malicious malware/tool. We can dump a process by specifiying its pid as an argument and dump argument in pslist plugin .
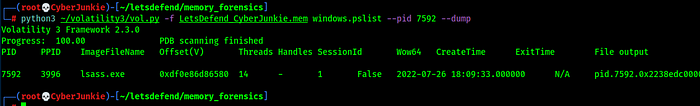
now we have the malicious binary on disk to analyze. I renamed the dumped binary for easing the process.
We verify that its malicious
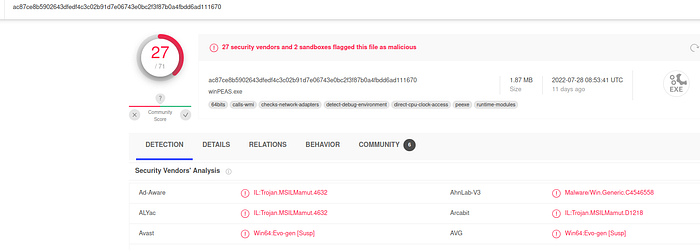
We see in virustotal details that it is winpeas.exe

Answer : Winpeas.exe
Q4 Which User Account was compromised? Format (DomainName/USERNAME)
To see usernames and domain name, we can use windows.session plugin which will show usernames and processes belonging to them .
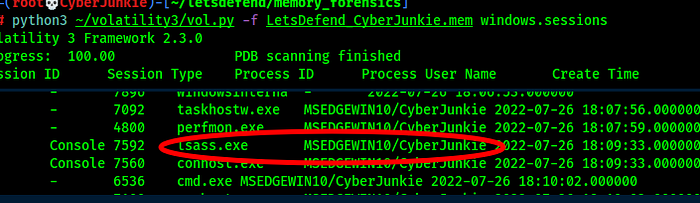
We can also see that legit lsass belongs to nt authority / system
Answer : MSEDGEWIN10/CyberJunkie
Q5 What is the compromised user password?
Volatility has a plugin named hashdump which works like mimikatzzzz. We can use that to dump the hash and then crack it
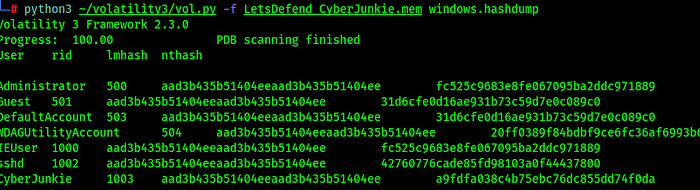
Compromised User is CyberJunkie, now we have access to this user’s ntlm hash we can crack it either with hashcat or john the ripper. WE can also crack it on crackstation.net website which i will be doing since my kali was having issue with it.
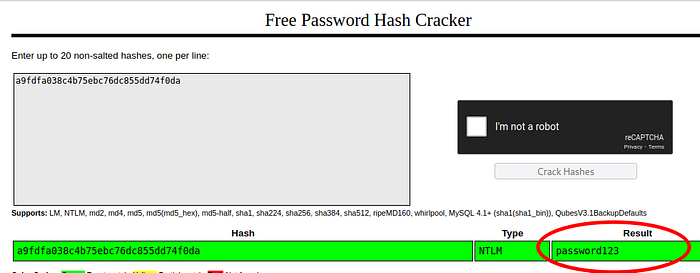
Answer : password123

